BYOK
Bring Your Own Key (BYOK) Support for PII data
About
Enterprise customers that wish to store highly sensitive information in Corsa are offered with our Sensitive Data Management feature:
-
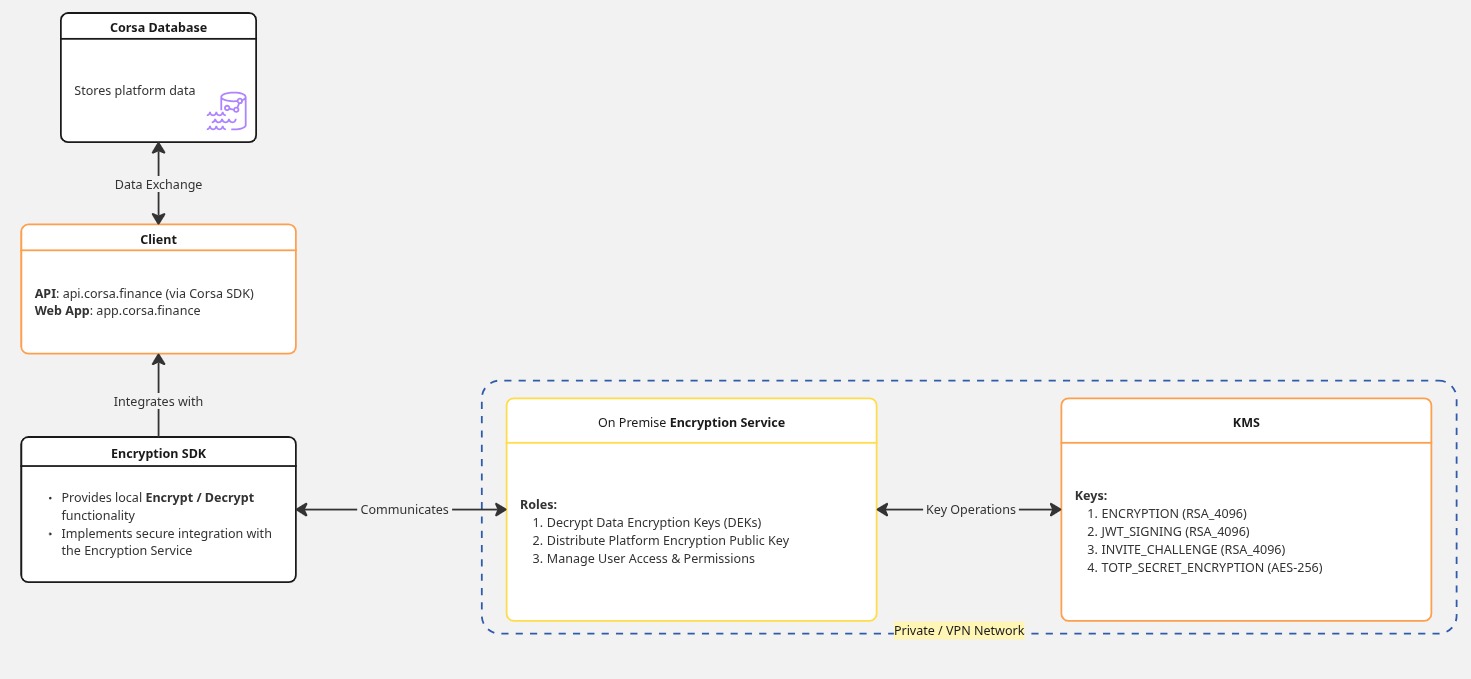
Enterprise customers can use their own AWS KMS keys for sensitive data encryption
-
Customers install the Corsa encryption service in their environment
-
The service connects securely to the customer’s AWS KMS
-
End-to-End Encryption Control
-
Sensitive data is encrypted and decrypted using the customer’s key
-
Encryption occurs on the customer’s side, ensuring full control and compliance
flow
System Requirements
- A modern Debian distribution (e.g. Ubuntu 24.04)
- 1 gigabyte of memory
- 1 gigabyte of storage
- nodejs 22.x
Networking
- Inbound TLS (typically port 443)
- Outbound traffic can be restricted to TCP port 443. (needed for JWT verification from auth0 and corsa)
KEYS
There are 4 keys used to encrypt data and handle 2fa
| name | type | description |
|---|---|---|
| JWT_SIGNING | SIGN_VERIFY | |
| INVITE_CHALLENGE | SIGN_VERIFY | |
| TOTP_SECRET_ENCRYPTION | ENCRYPT_DECRYPT | two factor authentication |
| ENCRYPTION | ENCRYPT_DECRYPT | PII encrypt / decrypt |
Cora currently supports AWS KMS at the moment
Setup
It is recommended to create the keys before launching an instance. See our Terraform guide as example.
Updated 6 months ago